Threat modeling is a proactive process that identifies potential attacks to an important asset so mitigations can be developed prior to any negative impact.
Building secure software is increasingly important to organizations. Regulators demand it, customers demand it, and leading companies understand that a documented and evidence-based secure development program can provide a competitive advantage.
Threat modeling can provide the foundation of such a program. This post introduces threat modeling, what it is, how it works, and its benefits.
What Are the Advantages of Threat Modeling?
You may find articles titled, “The Three Advantages of Threat Modeling” or “Six Reasons You Need to Threat Model.” The truth is that there are innumerable benefits to threat modeling.
To start, threat modeling helps improve the security posture of your product which will, in turn, reduce the security risk of your company.
It was Sir Francis Bacon who said, “Knowledge itself is power,” and the amount of security knowledge you (and your cross-functional teams) will gain from threat modeling your product is priceless.
It provides an opportunity to share different security perspectives, and that knowledge impacts every aspect of your product lifecycle from initial design to post-deployment support.
Threat modeling helps to reduce your attack surface. When you create a threat model – right from initial analysis (which may include a diagram) to suggested mitigations – your application is less vulnerable to attack.
Here Are 6 Advantages of Threat Modeling
- Identification of Threats and Countermeasures: Threat modeling aids in identifying potential threats to an application and prescribes corresponding countermeasures and security controls. This can span across software developers, security and operations teams, ensuring a comprehensive safeguarding approach.
- Anticipation of Threats: By prioritizing anticipation overreaction, threat modeling provides a proactive security approach. Instead of solely relying on security testing methods such as static analysis, dynamic analysis, software composition analysis and penetration testing, threat modeling anticipates potential threats even before the development phase begins.
- Prevention of Vulnerabilities: Through early anticipation of threats, organizations can prevent vulnerabilities even before they integrate into the application, leading to more secure software rapidly.
- Enablement of Secure Data Transmission: A common application threat includes the interception of sensitive data during transmission. Threat modeling offers countermeasures for such threats. For instance, implementing strong encryption ensures all sensitive in-transition data remains secure.
- Countering Brute Force Attack: Another potential application threat involves brute force attacks on user credentials. In response, threat modeling could prescribe countermeasures such as timing out a user’s login after three unsuccessful attempts.
- Regulatory Compliance: Threat modeling also considers legal and regulatory requirements. For example, if an application is subject to regulation like the Payment Card Industry Data Security Standard (PCI DSS), threat modeling would ensure that the development process incorporates these security standards.
Threat modeling is an exercise that identifies potential threats to an application and prescribes threat countermeasures and security controls for implementation by software developers, security, and operations teams.
In contrast to relying solely on security testing using static analysis, dynamic analysis, software composition analysis, and penetration testing, threat modeling anticipates threats prior to starting development.
This allows organizations to prevent vulnerabilities from entering the application and build secure software more rapidly.
For example, if the application is transmitting sensitive information, a threat is that an attacker could intercept that information. The threat countermeasure would be to use strong encryption to ensure that all sensitive data is encrypted when in motion.
Similarly, a threat could be a brute-force attack on user credentials. In that case, the threat countermeasure could be to time out a user’s login after 3 unsuccessful attempts.
Threat modeling also accounts for regulatory requirements.
When teams determine that an application is subject to a regulation like the Payment Card Industry Data Security Standard (PCI DSS) they will want to ensure that the security requirements of that standard are included in the development process.
What are the Popular Threat Modeling Techniques?
The threat modeling method you opt for directly aligns with your application’s unique needs. These methods vary greatly, each boasting its specific strengths and drawbacks to consider.
Historical threat modeling techniques such as the ‘Spoofing, Tampering, Repudiation, Information disclosure, Denial of service, and Elevation of Privilege’ (STRIDE) and ‘Process for Attack Simulation and Threat Analysis’ (PASTA) are still renowned for their meticulous manual methods.
Notably, STRIDE has been a reliable framework since its inception in 1999 by Microsoft.
In contrast, the ‘Common Vulnerability Scoring System’ (CVSS), developed by the ‘National Institute of Standards and Technology’ (NIST), often complements these traditional techniques, lending a more holistic approach to threat assessment.
Likewise, the application of attack trees further fortifies this comprehensive methodology, often used in combination with other threat modeling frameworks.
Other noteworthy methodologies making a significant difference in the cybersecurity landscape encompass:
- The Security Cards
- ‘Linkability, Identifiability, Non-repudiation, Detectability, Disclosure of information, Unawareness, and Non-compliance’ (LINDDUN)
- ‘Operationally Critical Threat, Asset, and Vulnerability Evaluation’ (OCTAVE)
- ‘Hybrid Threat Modeling’ (hTTM)
- ‘Quantitative Threat Testing Methodologies’ (Quantitative TTM),
- ‘Visual, Agile, and Simple Threat modeling’ (VAST)
It’s worth mentioning that every threat modeling methodology, old or new, plays a vital role in ensuring the best possible security measures are in place to tackle potential cyber threats.
Threat modeling automation software
As threats increase in complexity and severity, and the availability of skilled security resources decreases, threat modeling becomes even more crucial — and more difficult. So, we turn to automation and threat modeling software.
Threat Modeling Automation Software is essentially a digital tool designed to streamline and automate the process of identifying potential threats and strategizing countermeasures in a software development environment.
Instead of the traditional manual process where experts meticulously identify and manage threats, this software does it faster, more accurately, and on a larger scale.
As cyber threats grow in complexity, using automated tools helps safeguard software systems efficiently and effectively.
The best threat modeling tool facilitates cross-functional collaboration and includes the expert knowledge base required to recommend mitigations that address security weaknesses in your assets.
SD Elements is a threat modeling solution from Security Compass that has a proven 80 percent reduction in threat modeling time and a 92 percent reduction in vulnerabilities. SD Elements helps you automate the creation of common security mitigations that are typically derived from threat modeling analysis.
As a result, your cybersecurity risk is reduced early, quickly, and at scale.
Why Traditional Threat Modeling Fails and why Threat Modeling Software is Better
Traditional threat modeling is a manual exercise driven by specialized security and software architecture professionals.
Threat modeling teams can spend weeks mapping an application’s data flow, diagramming “trust boundaries,” and identifying mitigations for implementation by development teams.
While useful, traditional threat models bring several challenges:
- Scalability – Threat modeling is designed to protect applications across an organization’s portfolio. Security is only as good as its weakest link. Criminals will attack at the weakest point possible, then traverse an organization to steal sensitive data, conduct ransomware attacks, or disrupt operations.Allocating days or weeks for threat modeling exercises for every project is not practical in most organizations, even if the personnel can be found and retained.
- Flexibility – As an application evolves, so too does its threat model. Data flow and block diagrams may change, and diagrams can become increasingly incorrect. Manual threat models cannot be quickly updated.
- Consistency – Manual threat models are subject to the judgements, preferences, and expertise of those people building the models. While experienced personnel can apply consistency, their less experienced counterparts are likely to be less insightful and complete.
- Completeness and Auditability – The output from a manual threat model is usually a spreadsheet listing all identified threats and corresponding countermeasures. Tracking individual projects in discrete spreadsheets or shared documents complicates developers’ tasks and security’s role in validating hundreds of threat mitigation controls.
- Complexity – Applications become more complex each year. The adoption of microservices and complex APIs require special attention. The move to cloud platforms also demands the attention of security teams, as each platform presents unique risks that must be considered. Most organizations lack the depth of knowledge required to identify and mitigate risk from multiple threat vectors.
How Does Threat Modeling Impact Application Security?
Building secure software isn’t a secret. Development and security professionals have long known the steps required to prevent vulnerabilities in applications.
Unfortunately, we have long relied on developers to remember all these principles while facing relentless pressure to deliver software quickly.
Threat modeling helps teams identify potential threats based on an application’s development stack including programming languages and frameworks, deployment environments, and applicable internal security policies or regulatory standards.
Appropriate countermeasures and controls are then made part of the product requirements.
Threat modeling occurs before code is written, during the requirements and design phase of the Secure Development Lifecycle (SDLC).
This helps organizations build in Security by Design. Security through scanning and pen testing is difficult in a rapid development environment like DevSecOps or Continuous Integration | Continuous Deployment.
Scanners identify many issues that could have been avoided had appropriate countermeasures and controls been part of the product’s requirements. This is “reactive” security; responding to vulnerabilities instead of avoiding adding them to the code in the first place.
Threat modeling ensures that appropriate design patterns are adhered to, including least privilege principles, appropriate encryption algorithms, and consistent, approved controls.
Why should developers & managers care about Threat Modeling?
The role of development teams is to create software that not only performs effectively but also guarantees security. Functionality and safety are significant deliverables, especially within specific release timelines.
However, unanticipated alterations in the requirements mid-project can derail not only the workflow but also the delivery deadline.
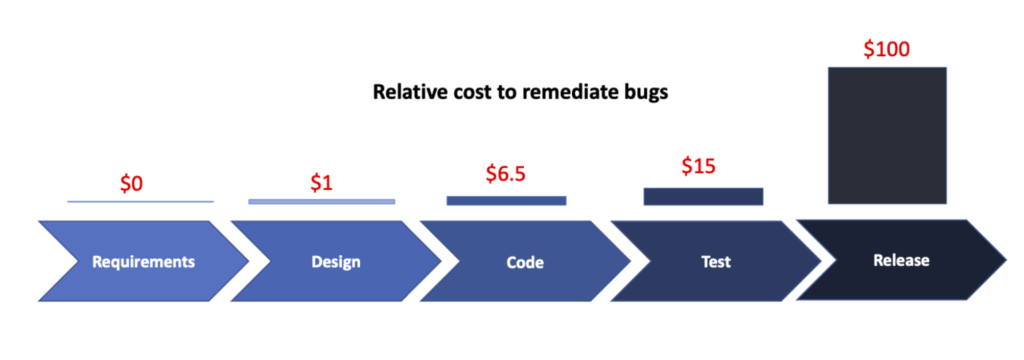
Moreover, the process becomes more challenging if security vulnerabilities emerge late in the Software Development Life Cycle (SDLC). Navigating these bugs becomes time-consuming, expensive, and impacts the overall project negatively.
To quantify, the Systems Sciences Institute at IBM indicates that the cost to rectify a bug discovered during the testing stage is 15 times higher than one unearthed during the design stage.
Hence, incorporating threat modeling from the onset of the project is vital. It helps teams anticipate and prevent vulnerabilities, leading to efficient development processes.
Additionally, it substantially reduces extra costs related to debugging and testing, proving to be not just a security measure, but a cost-effective, smart strategy as well.
Using threat modeling into the requirements phase of the SDLC allows development and security to reach agreement on how the application is built – including required mitigations and controls – and therefore more accurately forecast delivery commitments.
Threat Modeling as a Foundation for a Security Culture
A strong security culture is imperative to protecting an organization against security threats. This moves security to a collective responsibility instead of one of an individual or department. Threat modeling helps achieve this by bringing together all stakeholders, including security, development, operations, compliance, and product owners.
Threat modeling provides a clear picture of the risks inherent to an application and its deployment environment. This allows organizations to gain agreement on the steps they will take to mitigate risk and, since it is impossible to eliminate risk, achieve alignment on what represents acceptable risk.
By using threat modeling to identify the threats to an application, set clear objectives for the security posture required for an application, and define clear, consistent countermeasures during the design phase of the SDLC, all team members acknowledge and internalize the role of software security in the organization’s success.
You can learn more about how SD Elements automates threat modeling to scale software security across your entire portfolio, including its latest features, in our blog.