Static Version
Overview
Cybersecurity does not just rely on technical prowess to outwit threat actors but more critically, on the proactive approaches taken by humans in the digital loop. These include not only system personnel responsible for security but also system administrators, end users, and perhaps most critically, software developers who build and maintain software.
For developers, the phrase “it may not be your fault but it is your problem” comes to mind. Mindful of this, developers must consider several aspects beyond their code: (1) System thinking. Building and deploying software in cloud-based systems in particular requires moving beyond traditional “perimeter-based” cybersecurity defenses to “perimeter-less” cybersecurity frameworks, including zero trust architecture. (2) Proactive design.
Secure software development requires shifting security left to early design work and continuing through every stage of the SDLC. (3) Technical alignment. Agile methods allow security professionals to seamlessly integrate security activities into agile DevSecOps approaches. (4) Mature mindset and approach. Telling developers what checklists and processes to use along with errors to avoid, has some efficacy. However, engaging developers on security topics with a range of stakeholders elevates their thinking and approach. (5) Automation. The obvious should not be overlooked. Automated cybersecurity guidelines, training and guidance integrated into development streams are clearly beneficial.
The current research provide a comprehensive view into current developer views, including the challenges and opportunities they face in their secure development efforts. Specifically, it provides “deep dives” into issues of security maturity, threats, release states, gatekeeping, requirements, tools, resources, and training.
Demo/Firmographics
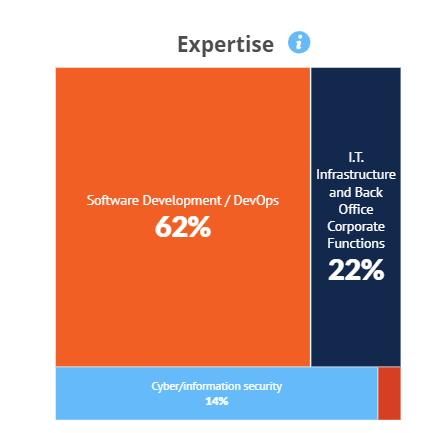
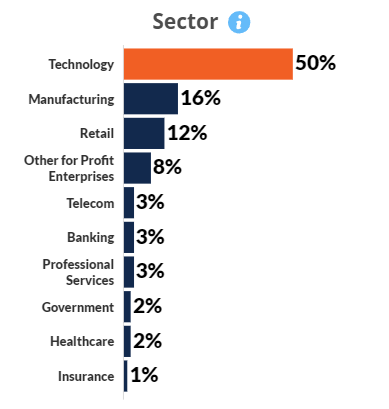
Developers were surveyed from companies that produce their own custom software. Respondents were part of the software development or Dev Ops teams, and in this capacity they must have been assigned requirements related to security and compliance and/or penetration testing. They came from a variety of industries and a range of company sizes.
Software Security Posture: Dev
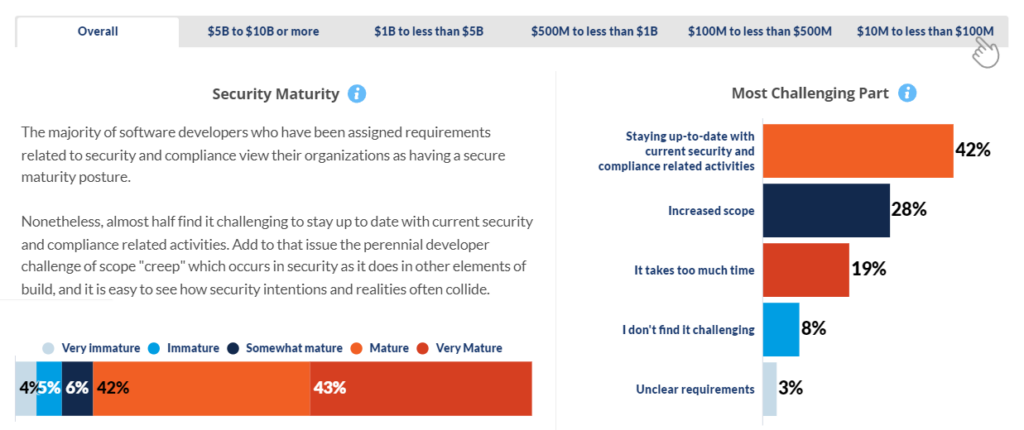
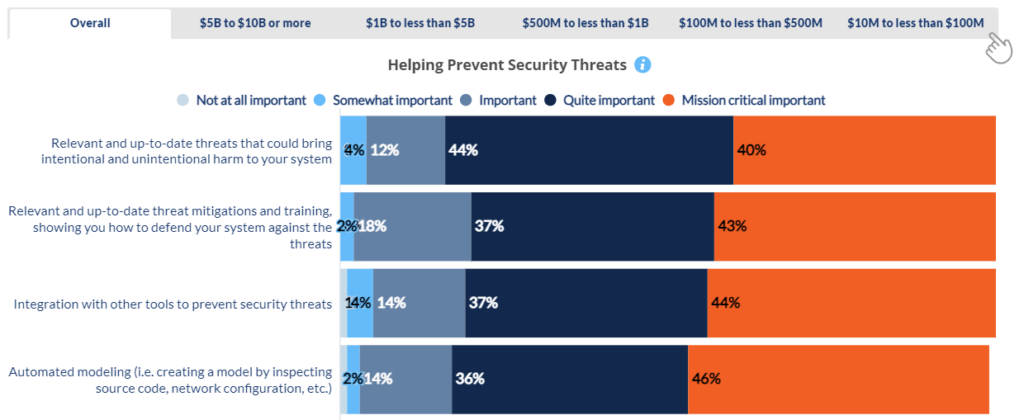
Security Threats
Automated modeling, integration with other tools, and matching the speed of new threats that emerge are all highly important to developers.
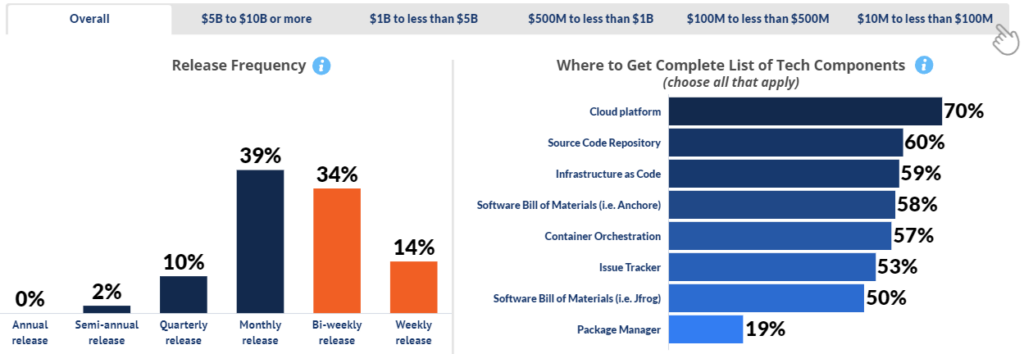
Software Release States
Most developers are working to release schedules of a month or less. Larger enterprises are less likely to do rapid, weekly releases versus smaller companies. Large companies also rely more on SBOM or container orchestration versus small companies relying on their cloud platform to identify the list of components used to build products.
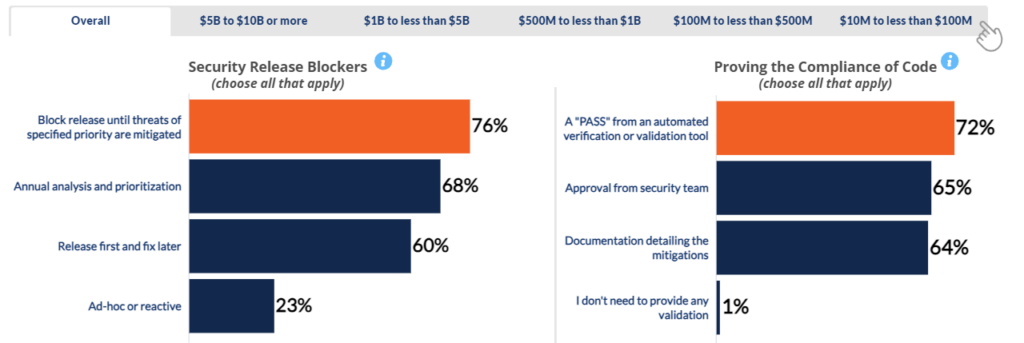
Software Release Gatekeeping
The majority of software developers report that their applications would not be released until threats of specified authority are mitigated. This finding held across all company sizes. By contrast, the smallest companies surveyed were more than twice as likely as the largest companies (31% vs. 14%) to use ad hoc or reactive means to gatekeep releases from a security perspective. Automated validation is key to most devs along with security team approval and documentation.
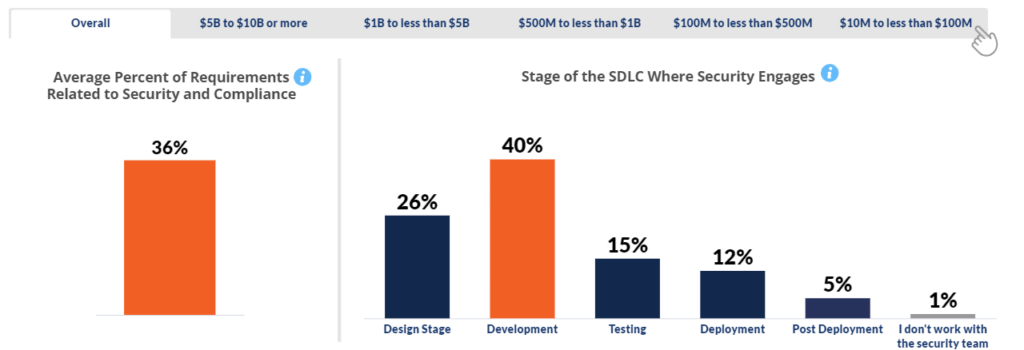
SDLC and Security Requirements
Developers surveyed reported a wide variation in the percent of their software requirements, user stories, and tickets in a typical release that were related to security and compliance. Surprisingly, on average a third of requirements were related to security and compliance. Only a quarter or so of companies have shifted security left into the Design Stage of software development, a finding that held true irrespective of company size. Overall, the Development stage dominates as to when security requirement are most likely to occur.
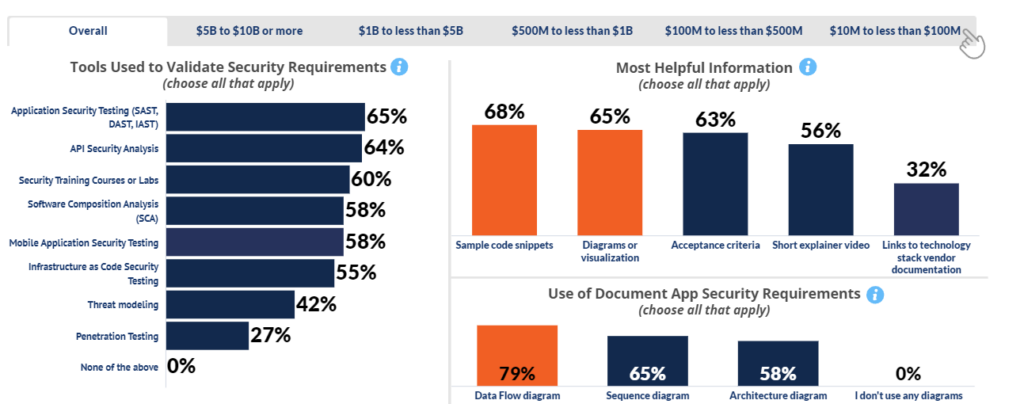
Tools and Helpful Information
Application security testing tools are #1, with the most helpful information provided typically being sample code snippets and data flow diagrams.
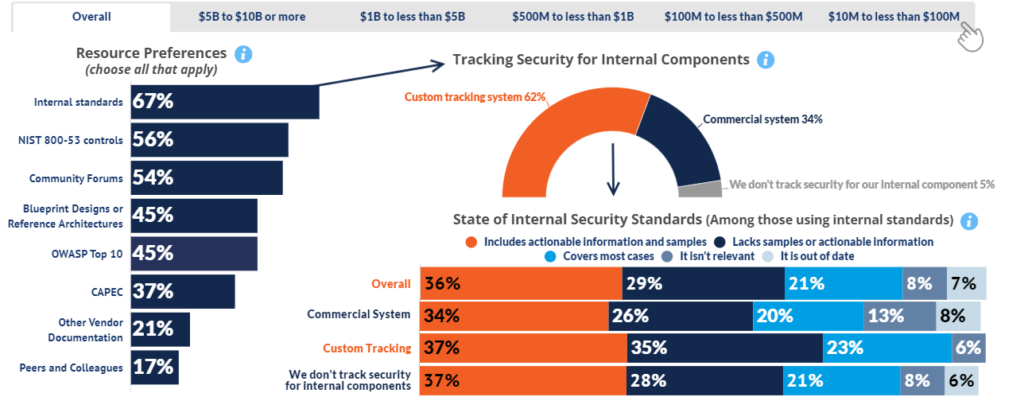
Resources
Resource preferences favor internal standards, of which almost two thirds involve custom tracking systems. Whether these in turn involve commercial systems or custom tracking systems, most are lacking actionable information and samples.
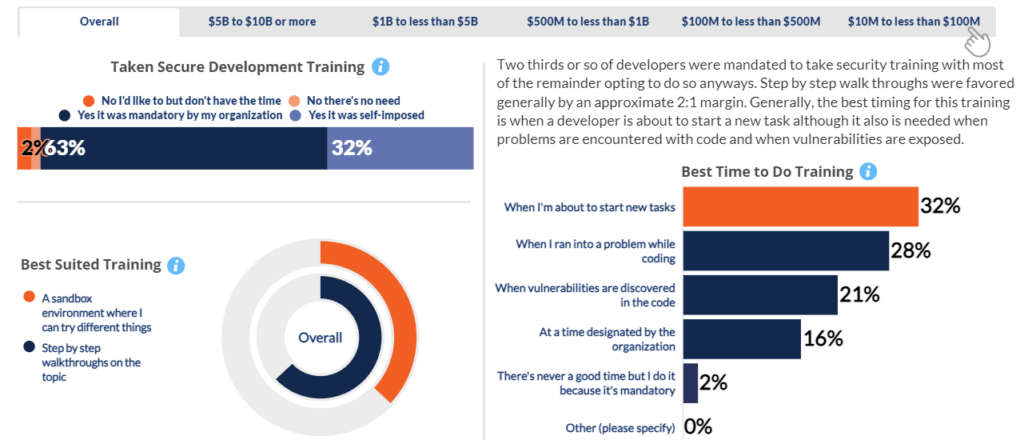
Training
Training (con’t)
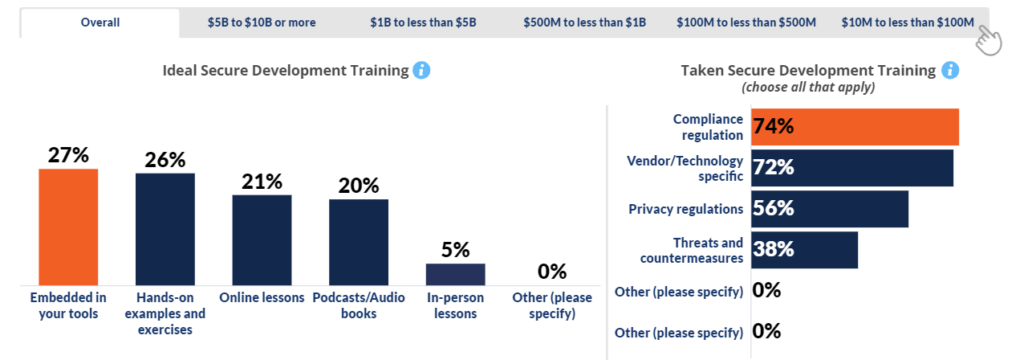
Further to desired training needs, having training embedded in tools was overall top ranked but of almost equal importance to developers is that they want hands-on examples, online lessons, and podcasts. Not surprisingly, software developers favor software in its various forms for their training versus in-person lessons. The majority want it for compliance regulation but it is also desired for vendor/technology specific applications.
Conclusion
Laying security issues at the feet of developers does little to abate the deluge of cybersecurity threats hitting enterprises across all sectors and of all sizes. Checklists, reminders and moral suasion to build carefully is not nearly adequate. Most developers involved in product builds believe their companies to have a mature security posture but nonetheless struggle to keep up to date with growing regulations and compliance requirements. On the cybersecurity front, developers view automated modeling, integration with other tools, and matching the speed of new threats that emerge as all highly important. Security must start with design and remain a critical element at each stage of the SDLC.
While working to release schedules of a month or less, developers rely first and foremost on Cloud platforms for lists of tech components although in larger enterprises also on SBOM or container orchestration. With most apps not released until threats of specified authority are mitigated, automated validation is key along with security team approval and documentation. Developers rely #1 on application security testing tools with the most helpful information typically being sample code snippets and data flow diagrams.
Resource preferences favor internal standards, of which almost two thirds involve custom tracking systems. Nonetheless, most lack actionable information and samples. Developers embrace training, whether mandatory or voluntary. Step by step walk throughs are favored generally by an approximate 2:1 margin. Generally, the best timing for this training is when a developer is about to start a new task although it also is needed when problems are encountered with code and when vulnerabilities are exposed.
Importantly, developers want training embedded in tools along with hands-on examples, online lessons, and podcasts. Not surprisingly, software developers favor software in its various forms for their training versus in-person lessons. Companies that want to attract and support developers in their efforts to build cyber-resilient software need to look to integrated cybersecurity software that provides just-in-time training (JITT) and guidelines for their software developers and automated cybersecurity software for accomplishing these goals.