Security by Design is a proactive approach to embedding security into every phase of the software development lifecycle. Once you have established the value drivers and created a compelling business case for Security by Design, the next crucial step is to build a program plan.
This plan should include clearly defined goals, a stakeholder engagement plan, and phased execution to ensure successful adoption and implementation. Here’s how to build an effective program plan for Security by Design.
Establishing Goals
Setting clear and measurable goals is the foundation of a successful Security by Design program. These goals should be derived from the value drivers and business case you have established.
We recommend conducting a goal-planning workshop with key stakeholders to ensure alignment and buy-in.
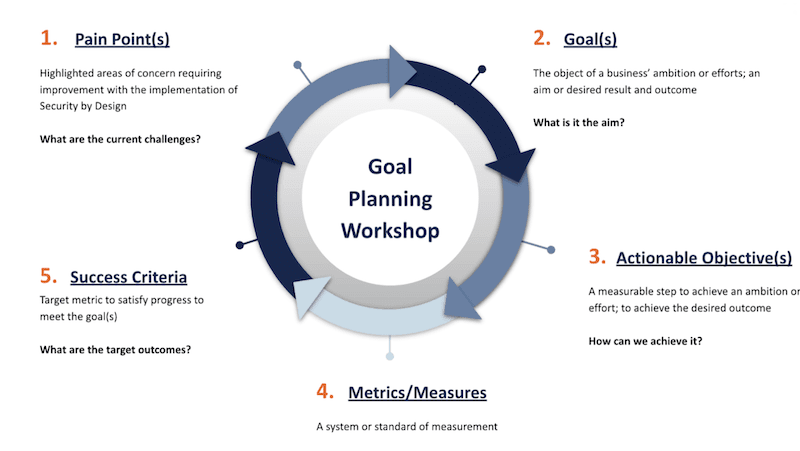
The Workshop Should Follow these Five Steps:
- Pain Points: Identify the specific pain points and challenges the Security by Design initiative aims to address. This includes understanding the current security gaps, vulnerabilities, and improvement areas.
- Goals: Define the overall goals of the Security by Design initiative. These should be broad, high-level objectives that align with the organization’s strategic priorities and address the identified pain points.
- Actionable Objectives: Break down the goals into specific, actionable objectives. These should be clear tasks and initiatives that can be implemented to achieve the broader goals. Examples include conducting regular threat modeling sessions, implementing secure code reviews, and providing secure coding training to developers.
- Metrics/Measures: Determine the metrics and measures that will be used to track progress and success. These should be quantifiable and include proactive metrics such as the number of threat models created, the percentage of secure code reviews completed, and the number of developers trained.
- Success Criteria: Establish success criteria to evaluate the effectiveness of the Security by Design program. This includes setting specific targets for each metric, such as reducing high-risk vulnerabilities by 50% within the first year and defining what successful implementation looks like for each objective.
Example Output From a Goal Planning Workshop:
- Pain Point: The current process of reviewing applications by a security team member results in a bottleneck and impacts our ability to ship software quickly
- Goal: Increase scalability of security design reviews
- Actionable Objectives:
- Use a Security by Design platform to perform design reviews for 10 applications.
- Metric: Number of applications onboarded; Target: 100%
- Measure the time taken in reviews using automation vs. manual process
- Metric: Time to complete process using automation, Target: 2 hrs. (vs. 40 hours manually)
- Use a Security by Design platform to perform design reviews for 10 applications.
- Success Criteria: Onboard at least 10 applications in 90 days and reduce security design review time by at least 300 hours in total.
Selecting Metrics and Targets
Selecting metrics and targets is one of the program’s most important aspects. As W.E. Deming said, “What’s measured gets done.” Often, application security programs only measure lagging and reactive metrics such as vulnerability count, defect density, and Mean Time To Resolution (MTTR).
If these are the only benchmarks for measurement, security and development teams may not be encouraged to work on Security by Design activities. This is because Security by Design takes time to implement and ultimately impacts the lagging indicators. Security requirements added to a backlog may take months or years to fully implement as they compete with user-facing features for development time.
Examples of Proactive Metrics Include:
For executive reporting, tie these metrics back to business value, such as reduced remediation costs, improved compliance, and enhanced risk management.
Start Your Security by Design
Journey Today
Gain instant access to our essential guide on Security by Design.
Click below to view or download your copy now.
Stakeholder Engagement
Creating a business case is just the beginning of launching a Security by Design initiative. It’s crucial to engage and gain buy-in from all relevant stakeholders. This can be achieved by outlining the key benefits for each stakeholder group and using a framework like INSPIRE to guide your engagement strategy:
1. Initiate
- Objective: Explain the need for Security by Design to the stakeholders.
- Action: Conduct initial meetings to highlight the importance and benefits.
2. Nurture
- Objective: Foster an understanding of each stakeholder’s roles and responsibilities in the program.
- Action: Provide training sessions and resources to build knowledge.
3. Support
- Objective: Offer continuous support and resources to stakeholders throughout the implementation.
- Action: Set up a help desk or support system for ongoing assistance.
4. Participate
- Objective: Engage stakeholders actively in the implementation process.
- Action: Involve them in planning sessions and decision-making processes.
5. Implement
- Objective: Execute the plan with the active involvement of all stakeholders.
- Action: Carry out the defined actions and strategies to embed Security by Design.
6. Review
- Objective: Regularly assess the progress and impact of the implementation.
- Action: Conduct periodic reviews and gather feedback from stakeholders.
7. Evolve
- Objective: Ensure continuous improvement and adaptation based on feedback and changing requirements.
- Action: Update the strategies and plans to address new challenges and opportunities.
Here are some Common Stakeholder Groups and their Benefits:
| Role | Responsibility | Common Motivators | Desired Outcomes |
| CISO, Chief Product Security Officer, or Security Leader |
|
|
|
| CTO or Development Leader |
|
|
|
| Application Security Team Member |
|
|
|
| Security Champion |
|
|
|
| Software Developer |
|
|
|
| Application Owner (Product Manager or Business Lead) |
|
|
|
| Application/Information Security Architect |
|
|
|
| Compliance and Risk Management Lead / Internal Audit |
|
|
|
Project Plan
The project plan for rolling out Security by Design will differ depending on the size and goals of your company. However, successful programs generally follow four phases of execution:
- Align: Create a detailed plan and ensure all stakeholders are aligned with the goals and responsibilities.
- Execute: Begin implementation with a pilot team, setting up tools and processes to test the approach.
- Realize: Expand the rollout based on feedback and results from the pilot phase, measuring impact and making necessary adjustments.
- Advocate: Advocate for the program across broader applications, leveraging successes from earlier phases to drive adoption.
Example Plan for a Large Enterprise
Phase 1: Align
- Conduct goal planning workshop
- Define scope, metrics, targets, responsibilities, and timeline
- Secure executive sponsorship
Phase 2: Execute
- Select a pilot team and application
- Implement Security by Design practices (e.g., threat modeling, secure code reviews)
- Gather feedback and refine processes
Phase 3: Realize
- Expand to additional teams and applications
- Measure and report on key metrics
- Adjust program based on feedback and results
Phase 4: Advocate
- Share success stories and case studies
- Conduct training and awareness sessions
- Drive continuous improvement and scale the program
Communication Plan
Effective communication is crucial for the successful rollout of Security by Design. Your communication plan should include multiple steps and channels to inform and engage all stakeholders.
Key Elements of the Communication Plan Include:
- Kickoff Meetings: Host one or more meetings to describe the program, answer questions, and set expectations.
- Mass Email: Send an email announcing the program to all stakeholders, soliciting participation (if voluntary), or describing necessary changes.
- Follow-up Emails: Send periodic emails to provide updates, share progress, and address concerns.
- Cascading Communication: Use security champions to drive follow-up communications within their teams.
- Additional Channels: To reinforce messages, utilize other channels such as Slack, one-on-one meetings, staff meetings, town halls, and leadership meetings.
- Wiki/Intranet Page: Create a central repository of information, including FAQs, training materials, and progress reports.
Your Communications Should Address the Following Themes:
- Why the organization is adopting Security by Design
- How success will be measured
- Which processes and tools will be used
- How existing processes will change
- Who is accountable for following the processes
- Stakeholder-specific benefits
- How to provide feedback
Conclusion
Building a comprehensive program plan for Security by Design is a strategic and detailed process. It involves setting clear goals, selecting the right metrics, engaging stakeholders, creating a phased project plan, and implementing an effective communication strategy.
By following these steps, organizations can ensure the successful adoption and implementation of Security by Design, ultimately leading to more secure, resilient, and compliant software systems. As cybersecurity threats continue to evolve, a proactive approach to security is essential for safeguarding digital assets and maintaining a competitive edge.